|
This tutorial quickly leads you through installing Joomla 1.5. It
details both a local installation for testing (if you do not have a
hosting account or have a slow internet connection) and a real web
server installation. Joomla is a complex series of PHP scripts that run on a web server. When you browse a Joomla site, these scripting are being generated on the fly and creating what you see on the pages of the site. The key words here are web server. Running and Testing Joomla Without a Hosting AccountYou cannot download Joomla and try to run it on your computer like an exe file. It has to have a web server, which means you need to have a hosting account. Sounds obvious, but I have had a couple of people if they needed windows XP to run Joomla!Now, before we shell out our hard earned money for a hosting account, there is something else you can do first. You can actually run a web server on your local computer, in other words, your desktop or laptop. This is known as having a localhost. It may sound like I just contradicted myself from the previous paragraph, but not quite. You canÂ’t "run" Joomla itself on your own computer, but you can install a localhost web server for it to "run on". What you need to pull this off is some software that runs Apache, PHP and MySQL on your computer. These are the same software packages that power websites. There are two popular ones, WAMP (www.wampserver.com/en/index.php) and XAMPP (www.apachefriends.org/en/xampp.html) and they are both free (PGL license) I am going to quickly run through setting up WAMP, not that this package is windows specific. Download WAMP from the above link, and then install it. It will create a folder c:/wamp/www Run WAMP, you should get a handy icon in your system tray:  You need the dial to be white to continue. Note if you run Skype, it interferes with WAMP and so you have to start WAMP without Skype running (and then start Skype if you need it) Now open a browser and go to localhost (no "www") You should see the following page:  If you are not seeing this then you should stop and figure out why. You have to get this page before you can proceed. The WAMP site has some helpful troubleshooting FAQ's and a forum. You should see your folder called "Joomla" in the list of Your Projects. Click on that folder and you will get taken to that "website". Installing a Joomla Site on a Hosting AccountSo let's assume you either have a hosting account, or are going to get yourself one. There are some minimum requirements for Joomla to run, and they are slightly different for the different versions.Here are the minimum requirements for Joomla 1.0
help.joomla.org/content/view/34/132/ For Joomla 1.5 it’s recommended you have PHP 4.4.3 or above (for enhanced security). A thread on the Joomla forums lists various hosting companies who are active Joomla community members. The list can be found at forum.joomla.org/index.php/topic,6856.0.html Note that from now on, the steps are more or less the the same whether you are installing Joomla on a localhost or on a remote web server. Getting the Joomla FilesThis part is easy. Head on over to www.joomla.org and you will see a link to the download section on the home page, it looks like this: The version number is the number given. This image shows that it's the 11th release in the 1.0 series. Or you can head straight to the Forge and you will see all possible downloads: forge.joomla.org/sf/frs/do/viewSummary/projects.joomla/frs All versions are here as well as various upgrades from one release to another, important if you already have an installation of Joomla. Important Note:You cannot upgrade from Joomla 1.0 to Joomla 1.5. There are significant enough changes in the code that simply over writing files would break your site. The developer team has carefully chosen to talk about migration."Joomla 1.5 does not provide an upgrade path from earlier versions. Converting an older site to a Joomla 1.5 site requires creation of a new empty site using Joomla 1.5 and then populating the new site with the content from the old site. This migration of content is not a one-to-one process and involves conversions and modifications to the content dump." dev.joomla.org/component/option,com_jd-wp/Itemid,33/p,107/ This has been a deliberate choice to minimize the number of users who might attempt the "overwrite the files" technique. More can be found in the forum: "Joomla 1.5 is so significantly changed from 1.0 that there is no 'upgrade' path. This is the reason that we are providing a migration path. The concept is to build a new site and to migrate data from the old site. Extensions need to be installed and configured as if the site is new. The core data migration does reconstruct menu items for core elements and also keeps core module records with configuration settings." David Gal - forum.joomla.org/index.php/topic,63232.0.html Unzipping the filesYou need to unzip, or unpack the big Joomla files you have onto your server. If you are running as a localhost, your server would be the WAMP directory mentioned above. If you are on a web host, you will need to upload the file and then unpack it. Perhaps the easiest way to do this is with cpanel. Almost all hosting companies provide it. Use your file manager to upload the zip file to public_html (or whatever you have on your host). You can then use file manager to extract the files.Note: I don’t recommend using Fantasico. Many hosts provide it but don’t always have the most current file releases. Installing Joomla through a Web BrowserIf you have got this far that means you have unzipped the Joomla package to either a remote web host or your local computer. Now for the fun stuff!Using your browser of choice (Firefox of course), navigate to the location of all the localhost/Joomla. You will see the first installation screen. Choose Language: Here is the first look at some of the internationalization features of Joomla 1.5, you can select amongst many languages for the installation instructions. Pre-Installation Check A critical part in the installation process, this checks if all the minimum system requirements are met. The first set are required minimums, if they are red (not met) then you need to find a new environment (change hosts), talk them into changing their environment (upgrading PHP for example). Note that the last item is a permissions issue on a file that is much easier to rectify. You can usually change permissions through the cpanel provided by your host. This tool is generally an industry standard. The second set is recommended settings. If you don't meet them you can still install Joomla but it you experience problems with functionality and security. Once you are green to go, click next. License Joomla is released under a GNU/GPL license. One of the most common questions regarding this license is “can I remove the footer link that says Powered by Joomla”. It’s actually perfectly OK to do this, you just have to keep the copyright statement in the source code. However, I would recommend that you keep the link. Why? Joomla is an open source project, it receives no funding from any kind of revenue from selling its software. The bottom line is that thousands of developers around the world are developing this software that you are using right now. If you had to buy it from a commercial company, it would cost tens of thousands of dollars, but you are getting it for free. In return, keep the link, it will help the project gain in popularity and grow. Don’t hide the fact that you are using Joomla, be proud of it! And don’t be concerned about any kind of SEO dilution with an extra link off your page. Links to authoritative sites actually help you SEO! OK, I’ll get off my soapbox now… Database Configuration This is one of the main pages of the installation process, it’s where you need to enter important information about the database that your Joomla site will use. Note you will see a drop down for the database type. Joomla 1.5 only really runs on SQL, but some of the foundation has been laid for the next release, 2.0, to use more types, for example Oracle. The hostname will almost always be “localhost” The Username and password will have been provided by your hosting company, usually in an email you got when you created the account. If you are installing on a localhost using WAMP or XAMPP, the Username is usually “root” and the password is nothing/blank. Once you have entered this information, click Get Privileges and the Joomla installer checks to see if that user has rights to create a database. You should see this message:  If you made an error, or the user does not have sufficient permissions, then you get this message (after a small delay):  If the user you have does not have permissions then you can ask your hoster to pre-create a SQL database for you to use. Available collations refer to various character sets available for different languages. When you click the button you get a list of what is available:  Pick a Database name for the SQL database that Joomla will use. Use some sort of name that is not confusing. Other scripts use SQL databases and before you know it you might have several on your server and will need to tell them apart. Don’t use spaces in the name. If you are running several Joomla sites but only have access to one database, you will need to use a table prefix to distinguish them. You’ll need to enter the prefix in the advanced settings (below) Note if your user did not have database creation privileges and you were provided with a database instead you would obviously put that in as the name. The advanced settings are concerned with what content the site starts with and also the table prefixes mentioned above.  If you have an existing site and you are reinstalling over the top, you will need to select Drop Existing Tables. If you need to keep a back of them, select Backup Old Tables. Using “jos” as a table prefix is conventional unless you have multiple sites in the same database. Main Configuration The Main Configuration page determines how you will insert content into your site. You have three choices:
Cross your eyes, close your fingers and click next. Hopefully you will see this screen  If you do get this result, you can investigate different language options, view the site or jump right to the administration of your site. If you donÂ’t get this page, then you have some work to do. Often issues arise because of server environments. If the solution is not obvious, a useful step is to copy the error message or the main part of it and then search for it both on the Joomla help forums, forum.joomla.org and in Google. The chances are if you get an error, someone else has before you. Source : http://www.compassdesigns.net/joomla-tutorials/how-to-install-joomla-15 |
Senin, 19 September 2011
How to Install Joomla 1.5
How to Install Joomla 1.5
Rabu, 14 September 2011
Viruses
The Eternal Struggle
Helen Butler, an Internet user in Randolph, Mass., was plagued. After opening an attachment in an email message she thought was from a friend, she started getting a slew of ecards from Blue Mountain, as many as 50 a day."This was one of the most frustrating experiences I have encountered. The Blue Screen of Death and system crashes are all minor annoyances compared to this," Butler says.
Butler was blasted by the Blue Mountain worm (W32.HLLW.Cult.C@mm) an irritating bug that masquerades as an ecard from popularand innocent site BlueMountain.com, but gives hackers free access to your computer once it's been launched.
Blue Mountain is part of the new trend in worm/viruses called blended threats. Blended threats combine aspects of viruses and hacker attacks to drill into your computer, often providing a back door for malicious programmers to hijack your system or steal your data.
"What used to be called a virus several years ago is now a virus and then some," says Timo Kissel of antivirus firm Symantec.
Recent wars and global crises have also led to a rise in politically motivated viruses, says Chris Beltoff of antivirus firm Sophos. Spats between India and Pakistan and the ongoing Israeli and Palestinian conflict have led virus writers to join the fray, he says, and your computer may end up as collateral damage.
"I think that people are very disgruntled about some political or religious issue are going to be heard through the use of malicious code," says Beltoff.
Fortunately, even blended threats fail before the might of a good antivirus program. Although it's always best to head off viruses before they attack, Butler successfully killed off the bug and hasn't had a relapse since. "I submitted this information to McAfee, my antivirus program, and within a few days I received a pop-up notification on my PC that the worm was detected and deleted and I have had no problems since," Butler says.
Vanquish Viruses
The best cure for a virus is not to get one. With that in mind, here are some tips for avoiding and curing what the experts call "malware": malicious, infectious software.Don't Open Those Attachments - The top method for malware to spread itself is still email. Elf bowling, screen savers, online greeting cards . . . folks, if you didn't actually ask for it, don't open it. Send an email message to the person who sent the attachment to you and find out if it's OK. Remember, worms can fake your friends' email addresses.
Ratchet Up Security - To prevent Web sites from infecting your computer, go to your Control Panel. Go to Internet Options (click Start, Settings, and Control Panel). Double-click Internet Options, click the Security tab, and click the Custom Level button under Custom. On the long list of options, change everything possible to Prompt or High Safety except for*Active Scripting*, which should remain set to Enable. (So many Web pages use scripting that to disable it would make it difficult to surf.) That way, when Web sites try to activate programs, your computer will generally ask you first. Refuse requests from sites you don't trust.
Get Antivirus Software - TechiWarehouse recommends any of the leading commercial antivirus programs, such as Norton Internet Security ($14.95) or McAfee VirusScan ($8.88). It's critically important to keep your antivirus software updated, so the now-expired trial version that came with your computer just won't do.
Pop-Ups: Saving Your Eyeballs
In the battle between Web surfers' eyeballs and advertisers' determination, one of the most annoying weapons is the pop-up ad. For the past few years, advertisers have been forcing their messages in front of your window of choice, with dubious results.At one point in 2001, pop-up king X10, which sells mini video cameras (http://www.x10.com, but don't encourage them by going there), was the fifth most viewed site on the Internet, according to research firm Jupiter MediaMetrix. X10 doesn't release its finances to the public, but anecdotally, TechiWarehouse couldn't find anyone who had actually bought anything from Xl0. The figures likely include numerous inadvertent visits as a result of clicking the ubiquitous pop-up ads.
"When we do surveys of people to find out what the most annoying things on the Internet are, pop-ups actually come out pretty high," said Tom Powledge of Symantec.
The most annoying form of pop-up ad is the mousetrap. Pioneered by porn sites, mousetraps open new windows when you try to close ads. Eventually, you have to quit your browser.
A close second in annoyance are those pop-up ads that appear to be system messages; they're just sleazy and spread fear. Any messagecontaining the word "optimize" that pops up while you're surfing is an ad, as are those "browser checkers" that claim you have security flaws in your system. Don't click the ads; click the X in the upper-right corner to close.
Along with pop-up ads go pop-under ads. Supposedly less annoying than pop-up ads, these windows appear under your main browser window, so they don't interrupt your browsing. But they do clutter your Taskbar with dozens of meaningless Internet Explorer windows, making it tough to find the right window when you have minimized Explorer.
Pop-up ads have been steadily increasing as a percentage of all Internet advertising, according to research firm Nielsen/NetRatings. By the first quarter of 2003, pop-up ads made up 4.8% of all Internet ads, up from only 1.8% a year previously. (The online ad market is still dominated by banner ads. And important for our returning visitors is to note is that TechiWarehouse is working onto eliminating pop-up ads on our site totally.)
But browser manufacturers and software companies are on top of the pop-up ad problem. Internet Explorer may dominate the browser world, but other browsers, such as Mozilla, Opera, and Apple's Safari, have responded to consumers' calls by making it simple to cancel pop-up ads. All three browsers detect attempts to open windows without a user's request and simply stop them.
"Our users really wanted the ability to control pop-up ad blocking," said Kurt Knight, Internet product manager at Apple. "This was one of the things we really wanted in our browser."
Once You Pop, You Can Stop
Pop-ups can be occasionally informative (Orbitz's pop-ups often show great air fares), but they're usually pretty annoying. Fortunately, there are several things you can do to disable invasive ads.Don't Encourage Them - If you dislike pop-up ads, don't click them. That'll send the message to advertisers that pop-up ads aren't an effective form of getting their messages out.
Ditch Explorer - Alternate browsers Mozilla (http://www.mozilla.org) and Opera (http://www.opera.com), and for the Mac, Safari (http://www.apple.com/safari), all provide antipop-up ad options.
Get A Pop-Up Stopper - IE partisans can buy separate pop-up blocker programs to smooth their surfing experiences. Comprehensive Internet security programs, including Zone Labs' ZoneAlarm Pro ($39.88) and Symantec's Norton Internet Security ($14.95), block pop-up ads, but if you want the ad-blocking features but don't want those programs' antivirus and personal firewall functions, we have previously tested and recommended Alexa's latest browser toolbar (http://www.alexa.com). ISP EarthLink also provides a free pop-up ad blocker to all of its subscribers.
Source : http://www.techiwarehouse.com/engine/6a876b0f/Can-There-Be-a-More-Annoying-Place-Than-This?
Spyware: A Growing Threat
Spyware: A Growing Threat
It may call itself a "browser helper" and fill your screen with ads or pump your Favorites list full of porn. Or it may quietly sit in the background, sending information about your surfing habits to advertisers without your permission.Spyware and browser hijackers are a growing problem on the Internet. These programs either automatically install themselves when you visit a Web site or piggyback on the installer of an existing program (such as popular file-sharing application Kazaa). Beyond imperiling your privacy, they can damage the stability of your PC, and they're often very difficult to remove.
"We have some anecdotal information that as many as 40% to 50% of the people who call into our tech support have some sort of spy- ware on their machines," says Jim Anderson of EarthLink.
Most of the spyware average Internet users run into exists to spread advertising. Programs, such as Gator and Cydoor, track your browsing habits, serving up ads to fit your preferences, and share the profits with free software vendors who let adware piggyback on their installers. Gator and Cydoor are annoying, but not necessarily harmful.
"Advertising spyware and adware spread with popular file sharing programs such as Kazaa, Imesh, and Grokster. As more people install these programs, they also install the spyware that pays for them," says Mike Healan, a spyware tracker who publishes a newsletter at http://www.spywareinfo.com.
Browser hijackers, on the other hand, are noxious. Sites such as Lop.com and Xupiter.com install toolbars, add Favorites, and change your home page, often without your permission. New .Net and WebHancer integrate themselves into your network settings, making them difficult to remove and potentially crashing your browser or your computer, according toHealan. "Lop.com will hijack your browser, and you'll end up with casino and porn links on your Desktop and in your Favorites. It's pretty nasty," says Michael Wood of antispyware firm Lavasoft.
The makers of Lop.com, C2 Media, claim that its software is always installed voluntarily. Every spyware expert we spoke to says that's not the case, and that on systems with low security settings, Lop.com simply walks in and takes over.
Then there are porn dialers, another kind of hijacker. If you get an email message or see a site that advertises "free porn" if you run a "viewer" or "dialer program," stay away. The viewer program will disconnect your dial-up line and try to reconnect to a service provider overseas, charging as much as $5 a minute to your phone bill. This is an old trick (we saw it back in 1999), but it's still going strong.
Smash Spyware
Keeping your Internet security settings high is the key to avoiding and disabling spyware. For now, ISPs don't provide antispyware tools, although EarthLink plans to introduce one later this year. Until then, here are some tips:Shields Up - Change your Internet security settings so nothing gets installed without your knowledge. Go to Internet Options (click Start, Settings, and Control Panel). Double-click Internet Options, click the Security tab, and click the Custom Level button under Custom. On the long list of options, change everything possible to Prompt or High Safety. That way, when Web sites try to activate programs, your computer will always ask you first. Refuse requests from sites you don't know and trust.
Wall It Off - Spyware tries to secretly talk to the Internet, so a personal firewall can help identify and foil malicious software. There are plenty of free firewall programs out there; in the past, we've recommended the free Sygate Personal Firewall (http://soho.sygate.com) and the Zone Labs ZoneAlarm (http://www.zonelabs.com).
Eliminate Explorer - Mozilla and Netscape are more resistant to browser hijackers and "helpful" toolbars. "Lop.com can infect Mozilla/Netscape, but only if you choose to run a downloaded installer," Healan says.
Disinfect and Destroy - Several freeware applications can rid your PC of spyware and browser hijackers. Healan recommends the free Spybot Search & Destroy (http://security.kolla.de). Another well-respected product is Lavasoft's Ad-aware (http://www.lavasoft.de/software/adaware), also free. Run these programs frequently to keep bad guys at bay.
Source : http://www.techiwarehouse.com/engine/6a876b0f/Can-There-Be-a-More-Annoying-Place-Than-This?
Internet Enemy No. 1
Spam: Internet Enemy No. 1
If you think you've been getting more spam recently, you're right. According to antispam company Brightmail (http://www.brightinail.com), which processed 55 billion messages in March 2003, the level of "Make Money Fast!" and "Naked Girls XXX" email messages has boomed to never-before-seen levels."We're definitely predicting that by the end of the year, more than 50% of all email will be spam," says Brightmail CEO Enrique Salem. "At some point spam, renders email useless."
The most offensive spam, of course, is porn spam-especially when it ends up in children's mailboxes. But finding the spammers can be nearly impossible, as the most explicit solicitations are sent out by fly-by-night, mom-and-pop Web site operations and foreign companies(especially firms in Russia), often using hijacked mail servers or other ways to cover their tracks.
At press time, 30 states had enacted some spam-regulation legislation (see Spam laws.com at http://www.spamlaws.com/state), and Washington is finally getting angry. In April, senators Conrad Burns (R-Mont.) and Ron Wyden (D-Ore.) reintroduced a bill to make it a federal crime to send spam with a false address. Rep. Zoe Lofgren (U-Calif.) has another bill requiring spammers to tag their messages in the subject line, and Sen. Charles Schumer (D-N.Y.) promised a third bill to create a national "do not email" list.
In early May, the FTC and state law enforcement officials announced 45 legal cases they'd opened against spammers, and with EarthLink's help, the state of New York charged the alleged "Buffalo Spammer," who had sent more than 825 million email messages, with identity theft and forgery.
But legislative remedies can only go so far. U.S. laws don't affect foreign spammers, and criminal spammers don't care much about the lawanyway. So the antispam software business is also booming; programs both ISPs (Internet serviceproviders) and individual computers run detect spam by detecting telltale words, phrases, or patterns.
The spam world is a lot like the virus world; as antispam software gets more effective, spammers come up with new strategies to avoid the filters. Spammers' latest tactic, according to Salem, is to embed invisible HTML (Hypertext Markup Language) codes between the words of their messages or turn pans of their message text into graphics; both tactics help them evade pattern-matching filters which rely on being able to read the text of a message to zap it. "These techniques weren't being used six months ago," Salem says.
Slam That Spam
Spam may seem unstoppable, but there are ways to prevent your inbox from ever again being exposed to what the FTC (Federal Trade Com-mission) tactfully refers to as "organ enlargement' solicitations.Complain, Three Ways - Lawmakers are responding to a wave of popular anger, and to keep them fighting spam, you have to keep their feet to the fire. Email your senators and representatives encouraging them to vote for the Schumer, Lofgren, and Burns-Wyden antispam laws. Then forward spam both to the FTC at uce@ftc.gov and to your ISP's abuse department, which is usually at abuse@yourispname.com. For instance, EarthLink's abuse department is abuse@earthlink.net. Use your mailer's forward command and don't delete any of the spam message; the good guys need all the header info to find the perpetrators.
Use a Spam Address - Keep your regular email address only for family and friends. Use a separate account (another screen name on AOL or a free account at Yahoo! or Hotmail) to fill out forms, post on discussion boards, and slap up onto Web pages. The spam address will get all the spam.
Obscure Your Name - If you have to put your email address on the 'Net, a report from the Center For Democracy & Technology (http://www.cdt.org) found that obscuring it helps. For instance, if your address is joe@aol.com, put on your page that it's "joe at a-o-l dot com" or even "xyzjoel23@Yaol.com without the xyz or the 123." It's a little bit of a puzzle, but it stumps the automatic address-harvesters spammers use to find you.
Use An Obscure Name - A common spam tactic, the dictionary attack, randomly emails common names and short combinations of letters, so using a complex email address, such as Redjoe30@aol.com, is better than just plain joe@aol.com.
Use An Antispam ISP - Many ISPs nowadays claim to filter spam, although some are better than others. When we compared AOL 8.0 to MSN 8, for instance, we found AOL received far more spam. The current gold standard of ISP antispam products is Brightmail, which AT&T WorldNet, EarthLink, MSN, Verizon DSL, and some smaller providers use.
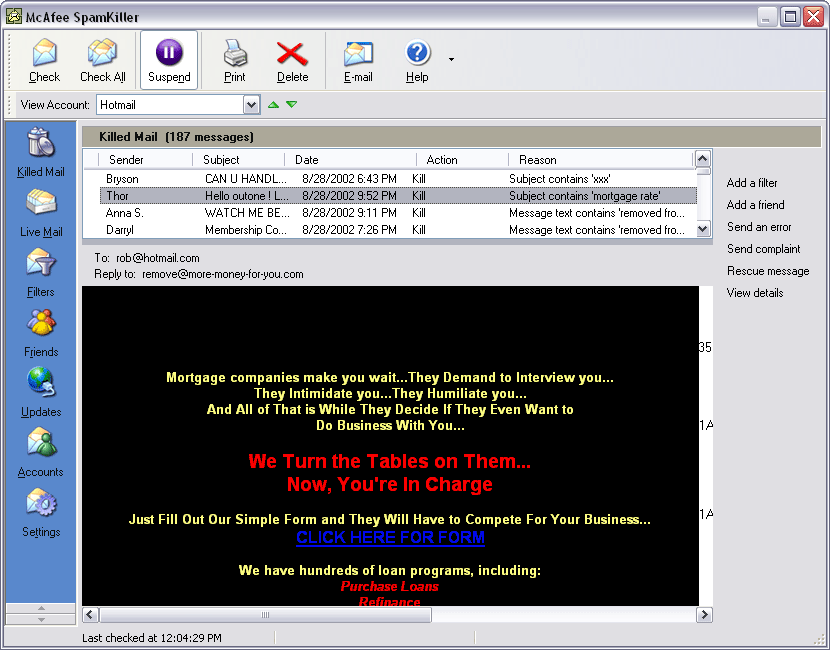
Get A Desktop Antispam Solution - Even the best ISP still misses some spam. For your PC, we recommend McAfee's SpamKiller ($22.00).
Hey, That's Not 56K
Your modem says 56Kbps (kilobits per second) on it, right? You think that means it'll connect to the Internet and transfer data at 57,600 bits per second? Wrong!"You'll never get a 56K connection on a dial-up connection. It just doesn't happen," says Rob Lancaster, Internet analyst at research firm The Yankee Group. "You're going to get 50Kbps, tops, depending on your Location."
It's actually impossible to get a 56Kbps connection (even if your computer claims it's happening), because the FCC restricts the voltage on phone lines so that only 53Kbps speeds are possible. And even if you're able to connect at 53Kbps, dial-up modems only receive information at 53Kbps, and you'll be sending data to the Internet at no more than 48Kbps.
If your connection is slow, don't blame your ISP. The problem is almost always in your phone line or in some piece of old, decaying phone company equipment, says Tom Pryzgoda, director of global marketing of modem manufacturer US Robotics.
"There are areas where they have equipment that's old, where the telecoms haven't been spending, and some people will never connect above 26.4Kbps," he says. "It's not the ISP; it's the phone line."
There are ways to speed things up even if you're connected at 26.4Kbps, though. Several ISPs have started to sell accelerated dial-up products, which compress text files and sometimes degrade graphics before they're sent to you, to speed up the appearance of Web pages. They don't speed up email messages, but that's probably fast enough already, they don't speed up streaming video or file downloads, but that's technically difficult if not impossible.
"When you go to a page that is predominantly text, it'll be the fastest," says Mark Goldstein, CEO of United Online, which runs the Juno and NetZero ISPs. "Whenever you're using a graphic, you won't see as much of a speed increase. But we're going to speed up your dial-up experience no matter what."
On the other hand, if you find yourself suddenly knocked offline in the middle of reading a long email message, there's usually something you can do about it. To make maximum use of their phone lines, ISPs often boot off anyone who hasn't exchanged data within the past 10 to 15 minutes. You can fool your ISP into keeping your connection alive with some simple software tricks.
If those tricks don't help, once again, your phone line's probably to blame. And phone companies are often less than enthusiastic about upgrading ancient copper cables to squeeze out a few more bits per second.
"In a lot of cases the phone company doesn't try to fix your analog line. They'll try to sell you DSL(Digital Subscriber Line) instead," Pryzgoda says.
Cure Connection Catastrophes
Whether you're getting cut off or just not getting the speed you deserve, there are several ways to make your Internet access speedier and more reliable.Keep It Alive - If getting cut off is your bane, set your email program to get mail every three minutes; that should prevent your ISP from thinking you've stepped away. Or use Gammadyne Software's freeware Connection Keeper (http://www.gammadyne.com/conkeep.htm) to keep your link alive.
Check The Lines - Switch to a different dial-up number, in case there's a problem on one of your ISP's lines. Then call your phone company and see if there's a problem on your line.
Optimize - There are various system settings you can change to speed up a dial-up connection. Or get a connection-optimizing program, such as High Mountain Software's iSpeed ($10.95 with 21-day free trial; http://www.hms.com).
Go External - If you're using an older computer with a so called win-modem, a built-in, software based modem, you may get better speeds if you buy an external modem. Win-modems are dependent on your computer's processing power, so if the computer is working too hard or memory is too full, you won't get great performance.
Accelerate - If most of your Internet use is Web surfing (as opposed to, say, downloading music) then a dial-up accelerator might help. Juno, NetZero, and EarthLink all offer accelerated services. If you have another ISP (including content provider AOL), you can use Propel Accelerator (http://www.propel.com).
Get Broadband - The only way to guarantee a fast, easy connection, all the time, is to switch to cable or DSL. As broadband providers like to remind you, high-speed access doesn't cost much more than a second phone line plus an Internet service, and it really does transform your 'Net experience into something much more pleasant.
Source : http://www.techiwarehouse.com/engine/6a876b0f/Can-There-Be-a-More-Annoying-Place-Than-This?
Sabtu, 10 September 2011
Examining your network with commands
Examining your network with commands:
PingPING is used to check for a response from another computer on the network. It can tell you a great deal of information about the status of the network and the computers you are communicating with.
Ping returns different responses depending on the computer in question. The responses are similar depending on the options used.
Ping uses IP to request a response from the host. It does not use TCP
.It takes its name from a submarine sonar search - you send a short sound burst and listen for an echo - a ping - coming back.
In an IP network, `ping' sends a short data burst - a single packet - and listens for a single packet in reply. Since this tests the most basic function of an IP network (delivery of single packet), it's easy to see how you can learn a lot from some `pings'.
To stop ping, type control-c. This terminates the program and prints out a nice summary of the number of packets transmitted, the number received, and the percentage of packets lost, plus the minimum, average, and maximum round-trip times of the packets.
Sample ping session
PING localhost (127.0.0.1): 56 data bytes
64 bytes from 127.0.0.1: icmp_seq=0 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=1 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=3 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=4 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=5 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=6 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=7 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=8 ttl=255 time=2 ms
64 bytes from 127.0.0.1: icmp_seq=9 ttl=255 time=2 ms
localhost ping statistics
10 packets transmitted, 10 packets received, 0% packet loss
round-trip min/avg/max = 2/2/2 ms
meikro$
The Time To Live (TTL) field can be interesting. The main purpose of this is so that a packet doesn't live forever on the network and will eventually die when it is deemed "lost." But for us, it provides additional information. We can use the TTL to determine approximately how many router hops the packet has gone through. In this case it's 255 minus N hops, where N is the TTL of the returning Echo Replies. If the TTL field varies in successive pings, it could indicate that the successive reply packets are going via different routes, which isn't a great thing.
The time field is an indication of the round-trip time to get a packet to the remote host. The reply is measured in milliseconds. In general, it's best if round-trip times are under 200 milliseconds. The time it takes a packet to reach its destination is called latency. If you see a large variance in the round-trip times (which is called "jitter"), you are going to see poor performance talking to the host
NSLOOKUP
NSLOOKUP is an application that facilitates looking up hostnames on the network. It can reveal the IP address of a host or, using the IP address, return the host name.It is very important when troubleshooting problems on a network that you can verify the components of the networking process. Nslookup allows this by revealing details within the infrastructure.
NETSTAT
NETSTAT is used to look up the various active connections within a computer. It is helpful to understand what computers or networks you are connected to. This allows you to further investigate problems. One host may be responding well but another may be less responsive.IPconfig
This is a Microsoft windows NT, 2000 command. It is very useful in determining what could be wrong with a network.This command when used with the /all switch, reveal enormous amounts of troubleshooting information within the system.
Windows 2000 IP Configuration
Host Name . . . . . . . . . . . . : cowder
Primary DNS Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Broadcast
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . :
WAN (PPP/SLIP) Interface
Physical Address. . . . . . . . . : 00-53-45-00-00-00
DHCP Enabled. . . . . . . . . . . : No
IP Address. . . . . . . . . . . . : 12.90.108.123
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . : 12.90.108.125
DNS Servers . . . . . . . . . . . : 12.102.244.2
204.127.129.2
Traceroute
Traceroute on Unix and Linux (or tracert in the Microsoft world) attempts to trace the current network path to a destination. Here is an example of a traceroute run to www.berkeley.edu:$ traceroute www.berkeley.edu
traceroute to amber.Berkeley.EDU (128.32.25.12), 30 hops max, 40 byte packets
1 sf1-e3.wired.net (206.221.193.1) 3.135 ms 3.021 ms 3.616 ms
2 sf0-e2s2.wired.net (205.227.206.33) 1.829 ms 3.886 ms 2.772 ms
3 paloalto-cr10.bbnplanet.net (131.119.26.105) 5.327 ms 4.597 ms 5.729 ms
4 paloalto-br1.bbnplanet.net (131.119.0.193) 4.842 ms 4.615 ms 3.425 ms
5 sl-sj-2.sprintlink.net (4.0.1.66) 7.488 ms 38.804 ms 7.708 ms
6 144.232.8.81 (144.232.8.81) 6.560 ms 6.631 ms 6.565 ms
7 144.232.4.97 (144.232.4.97) 7.638 ms 7.948 ms 8.129 ms
8 144.228.146.50 (144.228.146.50) 9.504 ms 12.684 ms 16.648 ms
9 f5-0.inr-666-eva.berkeley.edu (198.128.16.21) 9.762 ms 10.611 ms 10.403 ms
10 f0-0.inr-107-eva.Berkeley.EDU (128.32.2.1) 11.478 ms 10.868 ms 9.367 ms
11 f8-0.inr-100-eva.Berkeley.EDU (128.32.235.100) 10.738 ms 11.693 ms 12.520 ms
Source : http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
IP Addressing
IP Addressing:
An IP (Internet Protocol) address is a unique identifier for a node or host connection on an IP network. An IP address is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (known as octets) separated by decimal points. This is known as "dotted decimal" notation.Example: 140.179.220.200
It is sometimes useful to view the values in their binary form.
140 .179 .220 .200
10001100.10110011.11011100.11001000
Every IP address consists of two parts, one identifying the network and one identifying the node. The Class of the address and the subnet mask determine which part belongs to the network address and which part belongs to the node address.
Address Classes:
There are 5 different address classes. You can determine which class any IP address is in by examining the first 4 bits of the IP address.Class A addresses begin with 0xxx, or 1 to 126 decimal.
Class B addresses begin with 10xx, or 128 to 191 decimal.
Class C addresses begin with 110x, or 192 to 223 decimal.
Class D addresses begin with 1110, or 224 to 239 decimal.
Class E addresses begin with 1111, or 240 to 254 decimal.
Addresses beginning with 01111111, or 127 decimal, are reserved for loopback and for internal testing on a local machine. [You can test this: you should always be able to ping 127.0.0.1, which points to yourself] Class D addresses are reserved for multicasting. Class E addresses are reserved for future use. They should not be used for host addresses.
Now we can see how the Class determines, by default, which part of the IP address belongs to the network (N) and which part belongs to the node (n).
Class A -- NNNNNNNN.nnnnnnnn.nnnnnnn.nnnnnnn
Class B -- NNNNNNNN.NNNNNNNN.nnnnnnnn.nnnnnnnn
Class C -- NNNNNNNN.NNNNNNNN.NNNNNNNN.nnnnnnnn
In the example, 140.179.220.200 is a Class B address so by default the Network part of the address (also known as the Network Address) is defined by the first two octets (140.179.x.x) and the node part is defined by the last 2 octets (x.x.220.200).
In order to specify the network address for a given IP address, the node section is set to all "0"s. In our example, 140.179.0.0 specifies the network address for 140.179.220.200. When the node section is set to all "1"s, it specifies a broadcast that is sent to all hosts on the network. 140.179.255.255 specifies the example broadcast address. Note that this is true regardless of the length of the node section.
Private Subnets:
There are three IP network addresses reserved for private networks. The addresses are 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. They can be used by anyone setting up internal IP networks, such as a lab or home LAN behind a NAT or proxy server or a router. It is always safe to use these because routers on the Internet will never forward packets coming from these addressesSubnetting an IP Network can be done for a variety of reasons, including organization, use of different physical media (such as Ethernet, FDDI, WAN, etc.), preservation of address space, and security. The most common reason is to control network traffic. In an Ethernet network, all nodes on a segment see all the packets transmitted by all the other nodes on that segment. Performance can be adversely affected under heavy traffic loads, due to collisions and the resulting retransmissions. A router is used to connect IP networks to minimize the amount of traffic each segment must receive.
Subnet Masking
Applying a subnet mask to an IP address allows you to identify the network and node parts of the address. The network bits are represented by the 1s in the mask, and the node bits are represented by the 0s. Performing a bitwise logical AND operation between the IP address and the subnet mask results in the Network Address or Number.For example, using our test IP address and the default Class B subnet mask, we get:
10001100.10110011.11110000.11001000 140.179.240.200 Class B IP Address
11111111.11111111.00000000.00000000 255.255.000.000 Default Class B Subnet Mask
10001100.10110011.00000000.00000000 140.179.000.000 Network Address
Default subnet masks:
Class A - 255.0.0.0 - 11111111.00000000.00000000.00000000Class B - 255.255.0.0 - 11111111.11111111.00000000.00000000
Class C - 255.255.255.0 - 11111111.11111111.11111111.00000000
CIDR -- Classless InterDomain Routing.
CIDR was invented several years ago to keep the internet from running out of IP addresses. The "classful" system of allocating IP addresses can be very wasteful; anyone who could reasonably show a need for more that 254 host addresses was given a Class B address block of 65533 host addresses. Even more wasteful were companies and organizations that were allocated Class A address blocks, which contain over 16 Million host addresses! Only a tiny percentage of the allocated Class A and Class B address space has ever been actually assigned to a host computer on the Internet.
People realized that addresses could be conserved if the class system was eliminated. By accurately allocating only the amount of address space that was actually needed, the address space crisis could be avoided for many years. This was first proposed in 1992 as a scheme called Supernetting.
The use of a CIDR notated address is the same as for a Classful address. Classful addresses can easily be written in CIDR notation (Class A = /8, Class B = /16, and Class C = /24)
It is currently almost impossible for an individual or company to be allocated their own IP address blocks. You will simply be told to get them from your ISP. The reason for this is the ever-growing size of the internet routing table. Just 5 years ago, there were less than 5000 network routes in the entire Internet. Today, there are over 90,000. Using CIDR, the biggest ISPs are allocated large chunks of address space (usually with a subnet mask of /19 or even smaller); the ISP's customers (often other, smaller ISPs) are then allocated networks from the big ISP's pool. That way, all the big ISP's customers (and their customers, and so on) are accessible via 1 network route on the Internet.
It is expected that CIDR will keep the Internet happily in IP addresses for the next few years at least. After that, IPv6, with 128 bit addresses, will be needed. Under IPv6, even sloppy address allocation would comfortably allow a billion unique IP addresses for every person on earth
Source : http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Types of Servers
Types of Servers:
Device Servers
A device server is defined as a specialized, network-based hardware device designed to perform a single or specialized set of server functions. It is characterized by a minimal operating architecture that requires no per seat network operating system license, and client access that is independent of any operating system or proprietary protocol. In addition the device server is a "closed box," delivering extreme ease of installation, minimal maintenance, and can be managed by the client remotely via a Web browser.Print servers, terminal servers, remote access servers and network time servers are examples of device servers which are specialized for particular functions. Each of these types of servers has unique configuration attributes in hardware or software that help them to perform best in their particular arena.
Print Servers
Print servers allow printers to be shared by other users on the network. Supporting either parallel and/or serial interfaces, a print server accepts print jobs from any person on the network using supported protocols and manages those jobs on each appropriate printer.Print servers generally do not contain a large amount of memory; printers simply store information in a queue. When the desired printer becomes available, they allow the host to transmit the data to the appropriate printer port on the server. The print server can then simply queue and print each job in the order in which print requests are received, regardless of protocol used or the size of the job.
Multiport Device Servers
Devices that are attached to a network through a multiport device server can be shared between terminals and hosts at both the local site and throughout the network. A single terminal may be connected to several hosts at the same time (in multiple concurrent sessions), and can switch between them. Multiport device servers are also used to network devices that have only serial outputs. A connection between serial ports on different servers is opened, allowing data to move between the two devices.Given its natural translation ability, a multi-protocol multiport device server can perform conversions between the protocols it knows, like LAT and TCP/IP. While server bandwidth is not adequate for large file transfers, it can easily handle host-to-host inquiry/response applications, electronic mailbox checking, etc. And it is far more economical than the alternatives of acquiring expensive host software and special-purpose converters. Multiport device and print servers give their users greater flexibility in configuring and managing their networks.
Whether it is moving printers and other peripherals from one network to another, expanding the dimensions of interoperability or preparing for growth, multiport device servers can fulfill your needs, all without major rewiring.
Access Servers
While Ethernet is limited to a geographic area, remote users such as traveling sales people need access to network-based resources. Remote LAN access, or remote access, is a popular way to provide this connectivity. Access servers use telephone services to link a user or office with an office network. Dial-up remote access solutions such as ISDN or asynchronous dial introduce more flexibility. Dial-up remote access offers both the remote office and the remote user the economy and flexibility of "pay as you go" telephone services. ISDN is a special telephone service that offers three channels, two 64 Kbps "B" channels for user data and a "D" channel for setting up the connection. With ISDN, the B channels can be combined for double bandwidth or separated for different applications or users. With asynchronous remote access, regular telephone lines are combined with modems and remote access servers to allow users and networks to dial anywhere in the world and have data access. Remote access servers provide connection points for both dial-in and dial-out applications on the network to which they are attached. These hybrid devices route and filter protocols and offer other services such as modem pooling and terminal/printer services. For the remote PC user, one can connect from any available telephone jack (RJ45), including those in a hotel rooms or on most airplanes.Network Time Servers
A network time server is a server specialized in the handling of timing information from sources such as satellites or radio broadcasts and is capable of providing this timing data to its attached network. Specialized protocols such as NTP or udp/time allow a time server to communicate to other network nodes ensuring that activities that must be coordinated according to their time of execution are synchronized correctly. GPS satellites are one source of information that can allow global installations to achieve constant timing.Source: http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Network Topologies
Network Topologies:
What is a Network topology?
A network topology is the geometric arrangement of nodes and cable links in a LAN,There are three topology's to think about when you get into networks. These are the star, rind, and the bus.
Star, in a star topology each node has a dedicated set of wires connecting it to a central network hub. Since all traffic passes through the hub, the hub becomes a central point for isolating network problems and gathering network statistics.
Ring, a ring topology features a logically closed loop. Data packets travel in a single direction around the ring from one network device to the next. Each network device acts as a repeater, meaning it regenerates the signal
Bus, the bus topology, each node (computer, server, peripheral etc.) attaches directly to a common cable. This topology most often serves as the backbone for a network. In some instances, such as in classrooms or labs, a bus will connect small workgroups
Collisions:
Ethernet is a shared media, so there are rules for sending packets of data to avoid conflicts and protect data integrity. Nodes determine when the network is available for sending packets. It is possible that two nodes at different locations attempt to send data at the same time. When both PCs are transferring a packet to the network at the same time, a collision will result.Minimizing collisions is a crucial element in the design and operation of networks. Increased collisions are often the result of too many users on the network, which results in a lot of contention for network bandwidth. This can slow the performance of the network from the user's point of view. Segmenting the network, where a network is divided into different pieces joined together logically with a bridge or switch, is one way of reducing an overcrowded network.
Ethernet Products:
The standards and technology that have just been discussed help define the specific products that network managers use to build Ethernet networks. The following text discusses the key products needed to build an Ethernet LAN.Transceivers
Transceivers are used to connect nodes to the various Ethernet media. Most computers and network interface cards contain a built-in 10BASE-T or 10BASE2 transceiver, allowing them to be connected directly to Ethernet without requiring an external transceiver. Many Ethernet devices provide an AUI connector to allow the user to connect to any media type via an external transceiver. The AUI connector consists of a 15-pin D-shell type connector, female on the computer side, male on the transceiver side. Thickwire (10BASE5) cables also use transceivers to allow connections.For Fast Ethernet networks, a new interface called the MII (Media Independent Interface) was developed to offer a flexible way to support 100 Mbps connections. The MII is a popular way to connect 100BASE-FX links to copper-based Fast Ethernet devices.
 Network Interface Cards:
Network Interface Cards:
Network interface cards, commonly referred to as NICs, and are used
to connect a PC to a network. The NIC provides a physical connection
between the networking cable and the computer's internal bus. Different
computers have different bus architectures; PCI bus master slots are
most commonly found on 486/Pentium PCs and ISA expansion slots are
commonly found on 386 and older PCs. NICs come in three basic varieties:
8-bit, 16-bit, and 32-bit. The larger the number of bits that can be
transferred to the NIC, the faster the NIC can transfer data to the
network cable.Many NIC adapters comply with Plug-n-Play specifications. On these systems, NICs are automatically configured without user intervention, while on non-Plug-n-Play systems, configuration is done manually through a setup program and/or DIP switches.
Cards are available to support almost all networking standards, including the latest Fast Ethernet environment. Fast Ethernet NICs are often 10/100 capable, and will automatically set to the appropriate speed. Full duplex networking is another option, where a dedicated connection to a switch allows a NIC to operate at twice the speed.
Hubs/Repeaters:
Hubs/repeaters are used to connect together two or more Ethernet segments of any media type. In larger designs, signal quality begins to deteriorate as segments exceed their maximum length. Hubs provide the signal amplification required to allow a segment to be extended a greater distance. A hub takes any incoming signal and repeats it out all ports.Ethernet hubs are necessary in star topologies such as 10BASE-T. A multi-port twisted pair hub allows several point-to-point segments to be joined into one network. One end of the point-to-point link is attached to the hub and the other is attached to the computer. If the hub is attached to a backbone, then all computers at the end of the twisted pair segments can communicate with all the hosts on the backbone. The number and type of hubs in any one-collision domain is limited by the Ethernet rules. These repeater rules are discussed in more detail later.
| Network Type | Max Nodes Per Segment |
Max Distance Per Segment |
| 10BASE-T 10BASE2 10BASE5 10BASE-FL |
2 30 100 2 |
100m 185m 500m 2000m |
Adding Speed:
While repeaters allow LANs to extend beyond normal distance limitations, they still limit the number of nodes that can be supported. Bridges and switches, however, allow LANs to grow significantly larger by virtue of their ability to support full Ethernet segments on each port. Additionally, bridges and switches selectively filter network traffic to only those packets needed on each segment - this significantly increases throughput on each segment and on the overall network. By providing better performance and more flexibility for network topologies, bridges and switches will continue to gain popularity among network managers.Bridges:
The function of a bridge is to connect separate networks together. Bridges connect different networks types (such as Ethernet and Fast Ethernet) or networks of the same type. Bridges map the Ethernet addresses of the nodes residing on each network segment and allow only necessary traffic to pass through the bridge. When a packet is received by the bridge, the bridge determines the destination and source segments. If the segments are the same, the packet is dropped ("filtered"); if the segments are different, then the packet is "forwarded" to the correct segment. Additionally, bridges do not forward bad or misaligned packets.Bridges are also called "store-and-forward" devices because they look at the whole Ethernet packet before making filtering or forwarding decisions. Filtering packets, and regenerating forwarded packets enable bridging technology to split a network into separate collision domains. This allows for greater distances and more repeaters to be used in the total network design.
Ethernet Switches:
Ethernet switches are an expansion of the concept in Ethernet bridging. LAN switches can link four, six, ten or more networks together, and have two basic architectures: cut-through and store-and-forward. In the past, cut-through switches were faster because they examined the packet destination address only before forwarding it on to its destination segment. A store-and-forward switch, on the other hand, accepts and analyzes the entire packet before forwarding it to its destination.It takes more time to examine the entire packet, but it allows the switch to catch certain packet errors and keep them from propagating through the network. Both cut-through and store-and-forward switches separate a network into collision domains, allowing network design rules to be extended. Each of the segments attached to an Ethernet switch has a full 10 Mbps of bandwidth shared by fewer users, which results in better performance (as opposed to hubs that only allow bandwidth sharing from a single Ethernet). Newer switches today offer high-speed links, FDDI, Fast Ethernet or ATM. These are used to link switches together or give added bandwidth to high-traffic servers. A network composed of a number of switches linked together via uplinks is termed a "collapsed backbone" network.
Routers:
Routers filter out network traffic by specific protocol rather than by packet address. Routers also divide networks logically instead of physically. An IP router can divide a network into various subnets so that only traffic destined for particular IP addresses can pass between segments. Network speed often decreases due to this type of intelligent forwarding. Such filtering takes more time than that exercised in a switch or bridge, which only looks at the Ethernet address. However, in more complex networks, overall efficiency is improved by using routers.What is a network firewall?
A firewall is a system or group of systems that enforces an access control policy between two networks. The actual means by which this is accomplished varies widely, but in principle, the firewall can be thought of as a pair of mechanisms: one which exists to block traffic, and the other which exists to permit traffic. Some firewalls place a greater emphasis on blocking traffic, while others emphasize permitting traffic. Probably the most important thing to recognize about a firewall is that it implements an access control policy. If you don't have a good idea of what kind of access you want to allow or to deny, a firewall really won't help you. It's also important to recognize that the firewall's configuration, because it is a mechanism for enforcing policy, imposes its policy on everything behind it. Administrators for firewalls managing the connectivity for a large number of hosts therefore have a heavy responsibility.Network Design Criteria:
Ethernets and Fast Ethernets have design rules that must be followed in order to function correctly. Maximum number of nodes, number of repeaters and maximum segment distances are defined by the electrical and mechanical design properties of each type of Ethernet and Fast Ethernet media.A network using repeaters, for instance, functions with the timing constraints of Ethernet. Although electrical signals on the Ethernet media travel near the speed of light, it still takes a finite time for the signal to travel from one end of a large Ethernet to another. The Ethernet standard assumes it will take roughly 50 microseconds for a signal to reach its destination.
Ethernet is subject to the "5-4-3" rule of repeater placement: the network can only have five segments connected; it can only use four repeaters; and of the five segments, only three can have users attached to them; the other two must be inter-repeater links.
If the design of the network violates these repeater and placement rules, then timing guidelines will not be met and the sending station will resend that packet. This can lead to lost packets and excessive resent packets, which can slow network performance and create trouble for applications. Fast Ethernet has modified repeater rules, since the minimum packet size takes less time to transmit than regular Ethernet. The length of the network links allows for a fewer number of repeaters. In Fast Ethernet networks, there are two classes of repeaters. Class I repeaters have a latency of 0.7 microseconds or less and are limited to one repeater per network. Class II repeaters have a latency of 0.46 microseconds or less and are limited to two repeaters per network. The following are the distance (diameter) characteristics for these types of Fast Ethernet repeater combinations:
| Fast Ethernet | Copper | Fiber |
| No Repeaters One Class I Repeater One Class II Repeater Two Class II Repeaters |
100m 200m 200m 205m |
412m* 272m 272m 228m |
* Full Duplex Mode 2 km
When conditions require greater distances or an increase in the number of nodes/repeaters, then a bridge, router or switch can be used to connect multiple networks together. These devices join two or more separate networks, allowing network design criteria to be restored. Switches allow network designers to build large networks that function well. The reduction in costs of bridges and switches reduces the impact of repeater rules on network design.
Each network connected via one of these devices is referred to as a separate collision domain in the overall network.
Source : http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Jumat, 09 September 2011
TCP/IP Networks
TCP/IP Networks:
TCP/IP-based networks play an increasingly important role in computer networks. Perhaps one reason for their appeal is that they are based on an open specification that is not controlled by any vendor.What Is TCP/IP?
TCP stands for Transmission Control Protocol and IP stands for Internet Protocol. The term TCP/IP is not limited just to these two protocols, however. Frequently, the term TCP/IP is used to refer to a group of protocols related to the TCP and IP protocols such as the User Datagram Protocol (UDP), File Transfer Protocol (FTP), Terminal Emulation Protocol (TELNET), and so on.The Origins of TCP/IP
In the late 1960s, DARPA (the Defense Advanced Research Project Agency), in the United States, noticed that there was a rapid proliferation of computers in military communications. Computers, because they can be easily programmed, provide flexibility in achieving network functions that is not available with other types of communications equipment. The computers then used in military communications were manufactured by different vendors and were designed to interoperate with computers from that vendor only. Vendors used proprietary protocols in their communications equipment. The military had a multi vendor network but no common protocol to support the heterogeneous equipment from different vendorsNet work Cables and Stuff:
In the network you will commonly find three types of cables used these are the, coaxial cable, fiber optic and twisted pair.Thick Coaxial Cable
This type cable is usually yellow in color and used in what is called thicknets, and has two conductors. This coax can be used in 500-meter lengths. The cable itself is made up of a solid center wire with a braided metal shield and plastic sheathing protecting the rest of the wire.Thin Coaxial Cable
As with the thick coaxial cable is used in thicknets the thin version is used in thinnets. This type cable is also used called or referred to as RG-58. The cable is really just a cheaper version of the thick cable.Fiber Optic Cable
As we all know fiber optics are pretty darn cool and not cheap. This cable is smaller and can carry a vast amount of information fast and over long distances.Twisted Pair Cables
These come in two flavors of unshielded and shielded.Shielded Twisted Pair (STP)
Is more common in high-speed networks. The biggest difference you will see in the UTP and STP is that the STP use's metallic shield wrapping to protect the wire from interference.-Something else to note about these cables is that they are defined in numbers also. The bigger the number the better the protection from interference. Most networks should go with no less than a CAT 3 and CAT 5 is most recommended.
-Now you know about cables we need to know about connectors. This is pretty important and you will most likely need the RJ-45 connector. This is the cousin of the phone jack connector and looks real similar with the exception that the RJ-45 is bigger. Most commonly your connector are in two flavors and this is BNC (Bayonet Naur Connector) used in thicknets and the RJ-45 used in smaller networks using UTP/STP.
Unshielded Twisted Pair (UTP)
This is the most popular form of cables in the network and the cheapest form that you can go with. The UTP has four pairs of wires and all inside plastic sheathing. The biggest reason that we call it Twisted Pair is to protect the wires from interference from themselves. Each wire is only protected with a thin plastic sheath.Ethernet Cabling
Now to familiarize you with more on the Ethernet and it's cabling we need to look at the 10's. 10Base2, is considered the thin Ethernet, thinnet, and thinwire which uses light coaxial cable to create a 10 Mbps network. The cable segments in this network can't be over 185 meters in length. These cables connect with the BNC connector. Also as a note these unused connection must have a terminator, which will be a 50-ohm terminator.10Base5, this is considered a thicknet and is used with coaxial cable arrangement such as the BNC connector. The good side to the coaxial cable is the high-speed transfer and cable segments can be up to 500 meters between nodes/workstations. You will typically see the same speed as the 10Base2 but larger cable lengths for more versatility.
10BaseT, the “T” stands for twisted as in UTP (Unshielded Twisted Pair) and uses this for 10Mbps of transfer. The down side to this is you can only have cable lengths of 100 meters between nodes/workstations. The good side to this network is they are easy to set up and cheap! This is why they are so common an ideal for small offices or homes.
100BaseT, is considered Fast Ethernet uses STP (Shielded Twisted Pair) reaching data transfer of 100Mbps. This system is a little more expensive but still remains popular as the 10BaseT and cheaper than most other type networks. This on of course would be the cheap fast version.
10BaseF, this little guy has the advantage of fiber optics and the F stands for just that. This arrangement is a little more complicated and uses special connectors and NIC's along with hubs to create its network. Pretty darn neat and not to cheap on the wallet.
An important part of designing and installing an Ethernet is selecting the appropriate Ethernet medium. There are four major types of media in use today: Thickwire for 10BASE5 networks, thin coax for 10BASE2 networks, unshielded twisted pair (UTP) for 10BASE-T networks and fiber optic for 10BASE-FL or Fiber-Optic Inter-Repeater Link (FOIRL) networks. This wide variety of media reflects the evolution of Ethernet and also points to the technology's flexibility. Thickwire was one of the first cabling systems used in Ethernet but was expensive and difficult to use. This evolved to thin coax, which is easier to work with and less expensive.
Source:http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Network Architectures
Network Architectures:
 Ethernet
Ethernet
Ethernet is the most popular physical layer LAN technology in use
today. Other LAN types include Token Ring, Fast Ethernet, Fiber
Distributed Data Interface (FDDI), Asynchronous Transfer Mode (ATM) and
LocalTalk. Ethernet is popular because it strikes a good balance between
speed, cost and ease of installation. These benefits, combined with
wide acceptance in the computer marketplace and the ability to support
virtually all popular network protocols, make Ethernet an ideal
networking technology for most computer users today. The Institute for
Electrical and Electronic Engineers (IEEE) defines the Ethernet standard
as IEEE Standard 802.3. This standard defines rules for configuring an
Ethernet network as well as specifying how elements in an Ethernet
network interact with one another. By adhering to the IEEE standard,
network equipment and network protocols can communicate efficiently.Fast Ethernet
For Ethernet networks that need higher transmission speeds, the Fast Ethernet standard (IEEE 802.3u) has been established. This standard raises the Ethernet speed limit from 10 Megabits per second (Mbps) to 100 Mbps with only minimal changes to the existing cable structure. There are three types of Fast Ethernet: 100BASE-TX for use with level 5 UTP cable, 100BASE-FX for use with fiber-optic cable, and 100BASE-T4 which utilizes an extra two wires for use with level 3 UTP cable. The 100BASE-TX standard has become the most popular due to its close compatibility with the 10BASE-T Ethernet standard. For the network manager, the incorporation of Fast Ethernet into an existing configuration presents a host of decisions. Managers must determine the number of users in each site on the network that need the higher throughput, decide which segments of the backbone need to be reconfigured specifically for 100BASE-T and then choose the necessary hardware to connect the 100BASE-T segments with existing 10BASE-T segments. Gigabit Ethernet is a future technology that promises a migration path beyond Fast Ethernet so the next generation of networks will support even higher data transfer speeds.
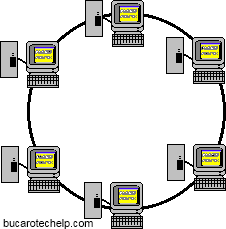 Token Ring
Token Ring
Token Ring is another form of network configuration which differs
from Ethernet in that all messages are transferred in a unidirectional
manner along the ring at all times. Data is transmitted in tokens, which
are passed along the ring and viewed by each device. When a device sees
a message addressed to it, that device copies the message and then
marks that message as being read. As the message makes its way along the
ring, it eventually gets back to the sender who now notes that the
message was received by the intended device. The sender can then remove
the message and free that token for use by others.Various PC vendors have been proponents of Token Ring networks at different times and thus these types of networks have been implemented in many organizations.
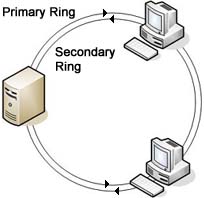 FDDI
FDDI
FDDI (Fiber-Distributed Data Interface) is a standard for data
transmission on fiber optic lines in a local area network that can
extend in range up to 200 km (124 miles). The FDDI protocol is based on
the token ring protocol. In addition to being large geographically, an
FDDI local area network can support thousands of users.Protocols:
Network protocols are standards that allow computers to communicate. A protocol defines how computers identify one another on a network, the form that the data should take in transit, and how this information is processed once it reaches its final destination. Protocols also define procedures for handling lost or damaged transmissions or "packets." TCP/IP (for UNIX, Windows NT, Windows 95 and other platforms), IPX (for Novell NetWare), DECnet (for networking Digital Equipment Corp. computers), AppleTalk (for Macintosh computers), and NetBIOS/NetBEUI (for LAN Manager and Windows NT networks) are the main types of network protocols in use today.Although each network protocol is different, they all share the same physical cabling. This common method of accessing the physical network allows multiple protocols to peacefully coexist over the network media, and allows the builder of a network to use common hardware for a variety of protocols. This concept is known as "protocol independence,"
Some Important Protocols and their job:
| Protocol | Acronym | Its Job |
| Point-To-Point | TCP/IP | The backbone protocol of the internet. Popular also for intranets using the internet |
| Transmission Control Protocol/internet Protocol | TCP/IP | The backbone protocol of the internet. Popular also for intranets using the internet |
| Internetwork Package Exchange/Sequenced Packet Exchange | IPX/SPX | This is a standard protocol for Novell Network Operating System |
| NetBIOS Extended User Interface | NetBEUI | This is a Microsoft protocol that doesn't support routing to other networks |
| File Transfer Protocol | FTP | Used to send and receive files from a remote host |
| Hyper Text Transfer Protocol | HTTP | Used for the web to send documents that are encoded in HTML. |
| Network File Services | NFS | Allows network nodes or workstations to access files and drives as if they were their own. |
| Simple Mail Transfer Protocol | SMTP | Used to send Email over a network |
| Telnet | Used to connect to a host and emulate a terminal that the remote server can recognize |
Source : http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Categories of Network
Categories of Network:
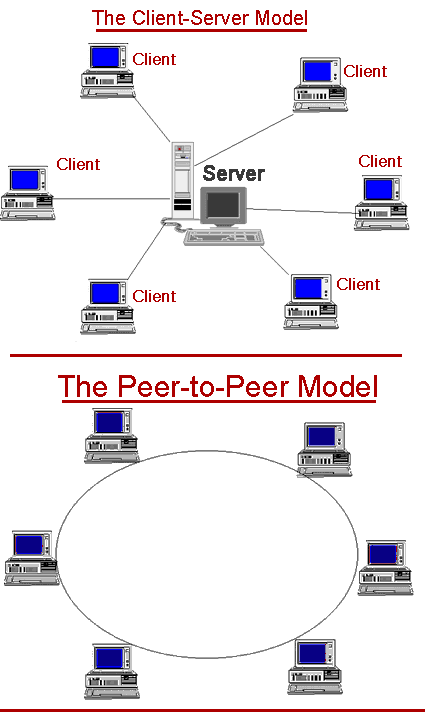 Network can be divided in to two main categories:
Network can be divided in to two main categories:
- Peer-to-peer.
- Server – based.
Peer-to-peer networks are good choices for needs of small organizations where the users are allocated in the same general area, security is not an issue and the organization and the network will have limited growth within the foreseeable future.
The term Client/server refers to the concept of sharing the work involved in processing data between the client computer and the most powerful server computer.
The client/server network is the most efficient way to provide:
- Databases and management of applications such as Spreadsheets, Accounting, Communications and Document management.
- Network management.
- Centralized file storage.
Client/server application design also lets the application provider mask the actual location of application function. The user often does not know where a specific operation is executing. The entire function may execute in either the PC or server, or the function may be split between them. This masking of application function locations enables system implementers to upgrade portions of a system over time with a minimum disruption of application operations, while protecting the investment in existing hardware and software.
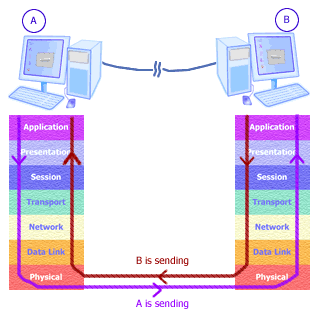 The OSI Model:
The OSI Model:
Open System Interconnection (OSI) reference model has become an
International standard and serves as a guide for networking. This model
is the best known and most widely used guide to describe networking
environments. Vendors design network products based on the
specifications of the OSI model. It provides a description of how
network hardware and software work together in a layered fashion to make
communications possible. It also helps with trouble shooting by
providing a frame of reference that describes how components are
supposed to function.There are seven to get familiar with and these are the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and the application layer.
- Physical Layer, is just that the physical parts of the network such as wires, cables, and there media along with the length. Also this layer takes note of the electrical signals that transmit data throughout system.
- Data Link Layer, this layer is where we actually assign meaning to the electrical signals in the network. The layer also determines the size and format of data sent to printers, and other devices. Also I don't want to forget that these are also called nodes in the network. Another thing to consider in this layer is will also allow and define the error detection and correction schemes that insure data was sent and received.
- Network Layer, this layer provides the definition for the connection of two dissimilar networks.
- Transport Layer, this layer allows data to be broken into smaller packages for data to be distributed and addressed to other nodes (workstations).
- Session Layer, this layer helps out with the task to carry information from one node (workstation) to another node (workstation). A session has to be made before we can transport information to another computer.
- Presentation Layer, this layer is responsible to code and decode data sent to the node.
- Application Layer, this layer allows you to use an application that will communicate with say the operation system of a server. A good example would be using your web browser to interact with the operating system on a server such as Windows NT, which in turn gets the data you requested.
Type Of Networks
What is a computer Network?
A network is any collection of independent computers that communicate with one another over a shared network medium. A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives. When networks at multiple locations are connected using services available from phone companies, people can send e-mail, share links to the global Internet, or conduct video conferences in real time with other remote users. When a network becomes open sourced it can be managed properly with online collaboration software. As companies rely on applications like electronic mail and database management for core business operations, computer networking becomes increasingly more important.- Every network includes:
- At least two computers Server or Client workstation.
- Networking Interface Card's (NIC)
- A connection medium, usually a wire or cable, although wireless communication between networked computers and peripherals is also possible.
- Network Operating system software, such as Microsoft Windows NT or 2000, Novell NetWare, Unix and Linux.
Types of Networks:
LANs (Local Area Networks)
A network is any collection of independent computers that communicate with one another over a shared network medium. LANs are networks usually confined to a geographic area, such as a single building or a college campus. LANs can be small, linking as few as three computers, but often link hundreds of computers used by thousands of people. The development of standard networking protocols and media has resulted in worldwide proliferation of LANs throughout business and educational organizations.WANs (Wide Area Networks)
Wide area networking combines multiple LANs that are geographically separate. This is accomplished by connecting the different LANs using services such as dedicated leased phone lines, dial-up phone lines (both synchronous and asynchronous), satellite links, and data packet carrier services. Wide area networking can be as simple as a modem and remote access server for employees to dial into, or it can be as complex as hundreds of branch offices globally linked using special routing protocols and filters to minimize the expense of sending data sent over vast distances.Internet
The Internet is a system of linked networks that are worldwide in scope and facilitate data communication services such as remote login, file transfer, electronic mail, the World Wide Web and newsgroups.With the meteoric rise in demand for connectivity, the Internet has become a communications highway for millions of users. The Internet was initially restricted to military and academic institutions, but now it is a full-fledged conduit for any and all forms of information and commerce. Internet websites now provide personal, educational, political and economic resources to every corner of the planet.
Intranet
With the advancements made in browser-based software for the Internet, many private organizations are implementing intranets. An intranet is a private network utilizing Internet-type tools, but available only within that organization. For large organizations, an intranet provides an easy access mode to corporate information for employees.MANs (Metropolitan area Networks)
The refers to a network of computers with in a City.VPN (Virtual Private Network)
VPN uses a technique known as tunneling to transfer data securely on the Internet to a remote access server on your workplace network. Using a VPN helps you save money by using the public Internet instead of making long–distance phone calls to connect securely with your private network. There are two ways to create a VPN connection, by dialing an Internet service provider (ISP), or connecting directly to Internet.Source : http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Turning on Wireless Zero Configuration
Turning on Wireless Zero Configuration
If you find that you can not connect to a wireless base station (such as Apple's Airport) because of issues with the configuration software provided by your wireless adapter's manufacturer. You may wish to uninstall that software (but keep the drivers) and use XP's native support for wireless networking.In order to do this you may need to turn on XP's wireless zero configuration.
Start -> Run

Type in services.msc

Click the OK button, which will bring up the following dialogue.

You may want to maximise the screen. Scroll down to Wireless Zero Configuration and select it.

You now have the option to Start the service.
You also need to change the Startup Type from Manual to Automatic
Action -> Properties

Click OK.
You can now use XP to manage your wireless connection.
Source : http://www.techiwarehouse.com/cms/engine.php?page_id=d9e99072
Langganan:
Komentar (Atom)